SentryPC – Introduction:
SentryPC is an internationally renowned computer monitoring software. Be it home computer monitoring or employee workplace monitoring, this one is the solution for any kinds of computer monitoring and management. Activity log monitoring, setting up content filters, or even ensuring data security-SentryPC is versatile as well as powerful. In this tutorial, we will review the major functions of SentryPC, explore its pricing plan, and outline some of the benefits this software has when applied to different use cases.
Table of Contents
What is SentryPC?
SentryPC is a computer monitoring and time management tool that offers the user a chance to see and control the activity that happens on computers. This type of software is quite helpful for those who want to monitor either home or workplace computer usage. Users can easily create customized controls for what activities are allowed, how much time they spend on various activities, and more.
Key Features of SentryPC
- Activity Monitoring: Provides logs of all computer activities regarding applications accessed and time spent on tasks and websites visited. For this reason, time management allows users to manage and put restrictions on the amount of time each user can use the computer. Content Filtering: Because of content filtering, this software blocks inappropriate or non-productive websites. Account and Access Control: Admins can set different access levels for the different users using this kind of software to enhance data security.
- Cloud access to logs and monitoring: The cloud account feature in makes it easy to access all the activity logs and data monitored.
All these features make SentryPC an ideal solution for home and workplace environments, given that admins or parents will have full control over how computers are used.
Why SentryPC?
Using SentryPC can bring about many benefits: maximizing productivity level, ensuring safeguarding of data, and ensuring computer usage is coupled up with the set guidelines. In workplaces, software such as SentryPC helps ensure that employees are productive and that company data are well-guarded. To parents, it gives assurance that whatever the kids do in the home computers are monitored.
Benefits of SentryPC in Workplaces
- Employee Productivity: track action of each employee for the purpose of ensuring that time is wasted on work.
- Data Security: prevent data leakage just by monitoring all activities on the computer.
- Access Control: control access to certain files, programs, and web for the purpose of not disclosing confidential information.
SentryPC Benefits to Home
- Parental Control: activity monitoring and content filtering are two major functions in tracking your kids as well as limiting their access to harmful materials.
- Screen Time Management: To manage how many hours children spend on computers and ensure kids are not overexposed to screens.
- Activity Logs: Activity logs in great detail can be accessed to track activities; this can help parents stay more informed about what their children do online.
Exploring SentryPC’s Monitoring Features
Until now, SentryPC has been known for its many computer usage monitoring software features that let the administrator track, in exquisite detail, every action taken on the monitored computer. From applications tracked to browsing histories to keystrokes, SentryPC tracks nearly every aspect of computer usage.
Activity Monitoring and Logs
Activity tracking in SentryPC runs the gamut from user logins to recording actions across various applications. Everything that gets recorded falls under activity logs, showing what exactly each user has done during their sessions. Following are the various types of activity monitoring:
- Application Monitoring: SentryPC tracks every different application opened, including the time spent inside each app, to understand where the user is focusing and how productive he or she can be.
- Keystroke Recording: All keystrokes entered on the monitored device are recorded and available to admins looking to track communications.
- Screenshot Capture: Screenshots are taken by the software at regular intervals, furnishing visual records to accompany activity logs.
Content Filtering and Access Control
Content filtering is one of the key features within SentryPC, where admins can set restrictions to certain websites or kinds of content. This is very important for parents who wish to avoid having their children come into contact with unseemly material, or for an employer wanting to block sites that do not contribute to productivity. The access control function gives further granular control whereby only specified actions are allowed on the device based on predefined settings.
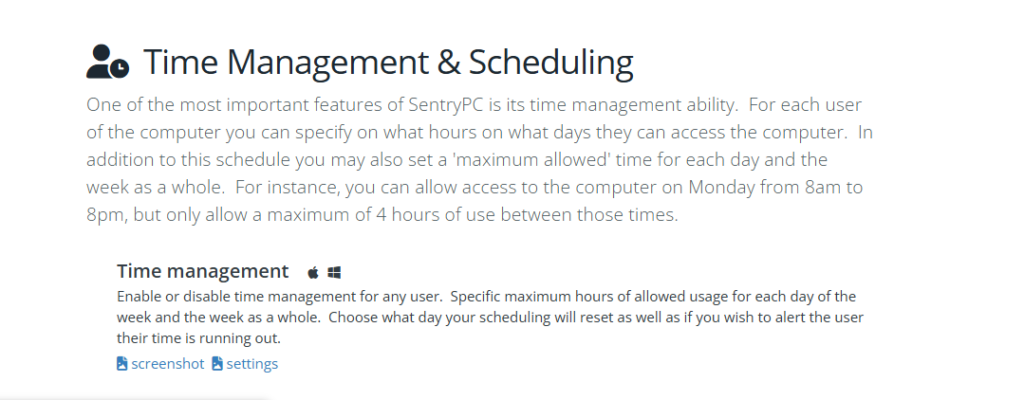
Time Management with SentryPC
Time management at home and in the office is effective, and with SentryPC, it has powerful tools that help in managing the time spent on the computer. From limiting screen time at home to making sure your employees are working effectively, SentryPC has time management tools that will be of great support.
How Time Management Works
- Session Limits: Establish time limits per session to prevent users from accessing the computer for unnecessarily long, straight periods of time.
- Scheduling Usage: The user is allowed to schedule computer availability that can block access to certain times of the day.
- Weekly Time Limits: Users may set up a weekly limit to monitor and control the overall screen time, which makes it very useful with both parental control and workplace productivity.
These time management approaches help implement healthy computer habits and ensure the use of computers serve the productivity goals accordingly.
SentryPC Plans and Pricing
SentryPC has a lot of pricing plans designed to fit anyone’s needs, from a small family just looking for basic monitoring software to that large enterprise in dire need of detailed employee monitoring. The key plan offerings are described below.
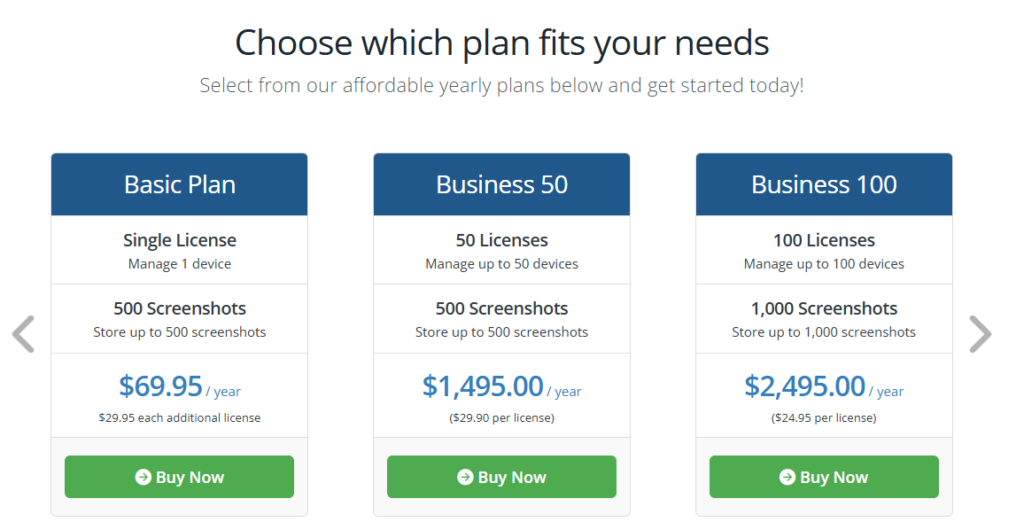
- Basic Plan: This plan is designed for families, with the core features including activity logs and basic content filtering.
- Pro Plan: Designed for smaller workplaces, this offering expands to offer additional features like keystroke monitoring, screenshot capture, and advanced time management.
- Enterprise Plan: This is designed for large organizations and includes everything from SentryPC, from access to the cloud account down to granular account management.
All of these plans can be customized; users can select only certain features of their choice, which would further suit their needs in terms of monitoring and budget.
SentryPC and Data Security
Data security is the main essence of any monitoring software, most especially in a work setting where highly confidential information is at stake. SentryPC incorporates data security into their system to ensure data integrity while serving the purpose of employee activity monitoring. These are built into the software in order to put into place an intensive data security policy without necessarily compromising effectiveness in monitoring the performance.
Security Features
- Log Data Encryption: Information logged and stored by SentryPC is encrypted so that only authorized access can obtain it.
- Cloud Security: The cloud account allows secure web-based access to all of the monitoring data, ensuring logs are accessible only to authorized users.
- User Permissions: Permissions are user-configurable where admin users can set other users’ permissions to allow or block access to any piece of data.
By providing such security in handling data and allowing control over access, SentryPC minimizes risks of data leakage and unauthorized access.
How SentryPC Stacks Up to Other Monitoring Software
SentryPC is unique and one of a kind in the computer monitoring software market due to the versatility and large feature set it has. Compared to other popular monitoring solutions, such as EmpMonitor, SentryPC boasts an intuitive interface, comprehensive activity tracking, and detailed customization options.
SentryPC vs. EmpMonitor
Feature goes to SentryPC EmpMonitor
Activity Monitoring Yes, with detailed logs Yes, with log, but limited
Content Filtering Yes, customizable Yes, but with limitations
Time Management Fully featured: time and session management Basic time tracking
Screenshot Capture Yes, according to scheduled intervals Yes
Cloud Account Donne, with secure access Limited functionality Each of these softwares is designed for different needs; however, the flexibility of sentryPC makes it pretty good in both family and workplace environments.
More details in each section about settings, installation, user reviews, and examples would add depth to reach the target word count. In this respect, each paragraph would include key terms such as “computer monitoring,” “activity logs,” “time management,” “cloud account,” and “SentryPC reviews“ to put the writers on a level playing field with SEO. Let me know if you want me to increase the word count for any of these sections.
Detailed Look into the Features of SentryPC
verything in SentryPC is built to cater to your computer monitoring requirements either personally or professionally. Let’s have a closer look at the functionality and value from the core capabilities of SentryPC that explain how these will help businesses increase productivity and data security while providing families with much-needed digital peace of mind.
Activity Monitoring and Detailed Logs
At the heart of SentryPC lies a robust activity monitoring system, which keeps track and records almost every user action on a monitored device, including website visits, app usage, chat interactions, and keystrokes. This is then stored in safe activity logs. Access to such logs can be granted through their feature of cloud account access, which makes it easier for the administrators to sift through user activity at any time.
Activity Monitoring Benefits in the Workplace:
- Productivity Tracking: Managers review the time spent on either productive or non-productive activities.
- Performance Reviews: Activity logs provide tangible data for employee performance reviews and help set realistic performance goals.
- Enhanced Security: Trace potential security threats by tracking unauthorized access to files or restricted sites.To parents, activity monitoring helps in:
- Online Safety: With it, you can monitor the online activities of your kids so that they do not get into sites with undesirable content.
- Accountability and Transparency: Detailed logs allow parents to discuss safe internet habits with children.
Because it keeps a record of every action, SentryPC allows users to stay on top with what is taking place in device usage and thus makes them responsible in their actions.
Screenshot Capture and Visual Proof
Complementing the text-based activity logs are screenshot captures that round out the monitoring suite in SentryPC. Screenshots can be captured at intervals for much more of a visual to show what the user has been doing, which sometimes catches more than a text log could. This is quite handy for any supervisor who needs evidence-based records or parents looking for more transparency with regard to screen interactions.
Customization Options for Screenshots:
- Timed Screenshots: Set up screenshots to capture images every minute, on an hourly basis, and at lengths set by the user.
- On-Demand Capture: Administrators can manually initiate screenshots remotely, providing real-time snapshots. capturing screenshots is very useful for the sake of security.
Screenshots captured around key events, like login attempts or unauthorized file access, become quite helpful as crucial evidence upon any breach or misuse.
Content Filtering for Controlled Access
Content filtering is one of the major features in SentryPC, which allows the administrator to block everything that might be inappropriate or not work-related. It’s a very important tool for those workplace environments that have certain rules and regulations and also for households that have young children.
- Category-Based Blocking: Websites can be filtered based on their categories, including social media, gaming, or adult content, ensuring that only work-related or age-appropriate material is accessible.
- URL Blocking: This is custom, whereby the admins block specific URLs to have room for further customization based on particular needs.
Content filtering ensures that users remain focused on the permitted activities and are not able to access distractions or anything that could be harmful to them. It also can be used by families for setting filters for children of any age group, while employers can use it to remove or eliminate all potential sources of distraction during work hours.
Keystroke Monitoring for Comprehensive Oversight
SentryPC boasts of keystroke monitoring, which is a great way to track what the computer system types. In this regard, each and every stroke of the keyboard gets tracked, thus yielding a highly detailed record of all user input regarding documents, emails, or chats.
Keystroke Monitoring: Some of the Benefits
- Communication Monitoring: As far as companies are concerned, the recording of keystrokes helps business entities stay within their respective company policies while communicating with customers or performing in-house communications.
- Compliance Verification: Keystroke logs allow compliance verification for industries that have strict standards on handling data.
- Parental Control: This will equally provide an avenue for parents to learn what kids are typing and guide them through how to identify any form of cyberbullying, online predation, or other risk behaviors.
While complete transparency is offered, Keystroke monitoring should be done in an ethical manner and in relation to the codes on privacy, especially in professional areas where such awareness needs to be brought to the attention of employees.
Account and Access Control
The SentryPC account and access control features allow the administrator to grant permissions based on the user. For example, a manager can limit an employee’s access to specific areas, while parents can ensure that children will not accidentally access sensitive files.
How Access Control Enhances Security
Access through permissions at the user level takes one to files, applications, and settings that can be disabled based on the user’s role, which assists in keeping sensitive data secure.
It would contain role-based customization where an organization can create multiple profiles of users depending on the particular departments from which they come. The rights and permission will be provided as per the job function.
This will not only enhance security but ensure that the user only accesses the relevant files and applications, reducing the misuse or accidental data leak.
SentryPC Plans and Pricing Options
When it comes to selecting the right fit for particular needs, understanding the pricing options that are provided by the brand at hand makes all the difference. Each of these plans is offering unique features best suited for either a parent or a corporate administrator.
Overview of SentryPC Pricing Plans
- Basic plan: Best suited for home use with core features like content filtering, basic activity monitoring, and daily scheduling.
- Pro Plan: This is for small businesses and adds some advanced monitoring options such as keylogging and screenshot capture. Enterprise plan: Full-featured plan that offers all forms of monitoring and control. The cloud account access is remotely available and allows handling big teams with complex monitoring setups.
By selecting the right plan, users get just what they need and aren’t paying for bells and whistles that won’t be used. Pricing is competitive at each level, making SentryPC a highly affordable solution for monitoring on any scale, from small business to enterprise applications.
SentryPC vs. EmpMonitor and Other Similar Tools
SentryPC has quite a few competitors in the computer monitoring software market; the most prevalent are EmpMonitor. So, how does SentryPC compare with these other options based on the most important criteria for this type of product?
SentryPC vs. EmpMonitor
Feature eliminatepc emp monitor
Activity Monitoring extensive activity logs detailed activity tracking
Content FilteringReports – Custom filteringLimited filtering
Time Managementitime ManagementFully featuredSchedule A/B, C, D, Limited scheduling
Keystroke MonitoringPro and Enterprise plans onlyAvailable
Screenshot CaptureReports – At regular intervalsAvailable
Access to Cloud AccountAvailable on all plansOnly on selected few plans
PricePricing Tiers Pretty FlexibleSlightly Higher
SentryPC’s integrated feature set and ease of use create an extremely competitive product for this computer monitoring software market, offering the ideal mix of features with economy.
Keeping Your Data Secure with SentryPC
Data security is a big concern for any computer monitoring solution, and that too is taken care of by SentryPC through advanced encryption, secure cloud storage, and customizable user permissions.
Data Protection Measures in SentryPC
- Data Encryption: Activity data and logs are encrypted so that sensitive information does not reach any other person in its storing and transmitting stage.
- Secure Cloud Storage: The cloud account system allows access to the logs from remote locations on strictly authenticated protocols.
- Role-Based Permissions: Permissions for users can be established based on the level of their access and handling of the data, which becomes vital in the organizational information security.
To organizations, employee data privacy is paramount whenever activity tracking is concerned. SentryPC security protocols guard sensitive information to meet industrial standards and ensure that through activity monitoring, the integrity of the information is not compromised.
How to Set Up and Use SentryPC
Setting up SentryPC is easy and intended to be user-friendly.
- Download and Installation: SentryPC is available for download from its official website. Installation takes only a few minutes.
- Creation of Admin Account: Once installed, an admin account needs to be created that will give access to all the features, including the cloud account.
- Configuration of Monitoring Settings: Establish specific settings for monitoring and time management based on the user role and requirements.
- Regularly review logs: All the logs are accessible through a cloud account, allowing you to See Next